There is something that most hackers nowadays don't pay much attention to, and thats Exploiting the host after you Exploit the host, for me this is why I'd be interested in breaking into a computer, because of the information that will be available on the host!
What I'm going to talk about is one way you can use Google's cache to extend the life of a hack,
but this is often only possible if you have already:
here the hacked defaced the site, it got cached but when I looked for it using the cache: directive, I found one cached much much older!! My theory is that this can happen the other way around!!
Leveraging this is into a replay is as easy as parsing the link if you need to, and feeding it to users of the site. But because of the way the cache: directive works, you don't need to parse or feed the actual link to the malicious application, you could simply feed them this link:
Tweet
What I'm going to talk about is one way you can use Google's cache to extend the life of a hack,
but this is often only possible if you have already:
- Stolen Cookies/logins off a host using XSS or Cross Site Request Forgery or (CSRF)
- Edited the page to perform HTTP parameter pollution/HTTP Response splitting via victim
Before I tell you the good news I need to make sure you're clued up on the cache, if you are by all means skip the next paragraph.
How the cache works
Google's cache is a storage area Google uses to reduce searching times by saving/storing a version of the page every now and then (often at intervals of a month) on a certain server so it can make comparisons with your search query and the cached version (classic space/time trade-off!), you can search the cache using the 'cache:' directive in you search query, and if a version is found it will immediately open that cached version on your browser.
Caching in on the Cache
You'll notice that the previous section has some bolded text it in it:
- A cached version of a web page can spend a long time in the cache
- The cached version is saved immediately from a search query
What does this mean to hackers? Well if you compromise a host, and make a lot of noise chances (i hope for the sake of humanity) are slim that it will go unnoticed for a long time, when it does get noticed, the developer fixes the page and goes on with his life knowing the users are now safe again!
Wrong!! and this is why...
if it so happens that
- you managed to edit the source of the page so that you can do something malicious.
- the malicious version of that page was cached
You can replay your malicious page over and over again using the Google cache server!!
And get this, you can do it completely undetected!!
Time Travel
So you have hacked and edited the page and your hack as been undone, how do you get the exploited version of the page?
- wait a couple of months, depending on the page rank of the page
- Search the google cache
the example I use here is actually the reverse of what time discussing, but it proves that the reverse is possible
Here's an example of a hacked server I found using a google derived from one of exploit DB's joomla exploits
- inurl:"*option=com_discussions*"+ inurl:"*catid=*" + inurl:*thread=*" intext:"Hacked by" ---this one is slightly improved...
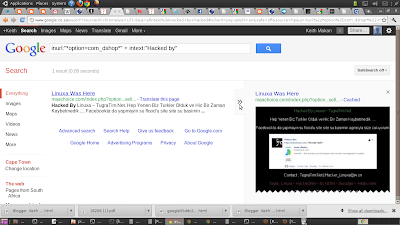 |
| The results, showing one cached version |
 |
| Results from the actual cache are older!! |
Leveraging this is into a replay is as easy as parsing the link if you need to, and feeding it to users of the site. But because of the way the cache: directive works, you don't need to parse or feed the actual link to the malicious application, you could simply feed them this link:
- http://www.google.co.za/search?q=cache:[hacked page URL]
What will happen is Google will automatically redirect you to the cached version of the Hacked page, if you dont believe me try the same thing for http://www.exploit-db.com
enter this in you address bar:
- http://www.google.co.za/search?q=cache:http://www.exploit-db.com
works right!!?? Plus all the javascript (and i think flash runs aswell!)
Thanks for reading!! Be more creative with this!!
Another couple of ideas I going to work on is:
ReplyDelete*Using this for DDoS (maybe possible) ---- thanks to @(www.twitter.com/Fabiothebest89)
*And what happens when malicious js is hosted on the cache and included in an exploited web application, will Google report this??
visit http://bypassthesecurity.blogspot.com
ReplyDelete